In this issue:
Threat of the week: BADBOX 2.0 botnet on your IoT home devices
Toll fee scam: What you can learn from it
Let me know if there’s a topic you want me to cover
FBI warning: BADBOX 2.0 botnet on your IoT home devices
Do you want to help criminals? No, I didn't think so. But if you have compromised Internet of Things (IoT) devices on your home network such as smart TVs, that's exactly what you are doing.
This week the FBI issued a warning for the something called BADBOX 2.0. Yes, there was a version 1.0 and now the criminals have improved on it.
BADBOX is a botnet. A botnet is when different computer programs work together to do something. For example, your smart TV can be infected with malicious software (malware) that forces it to act as a "bot" (like a robot) to attack websites or services on the internet. Botnets have even brought down parts of the internet itself.
We have to stop helping criminals. Don't let your IoT devices be part of a botnet.
The FBI states, "Cyber criminals gain unauthorized access to home networks through compromised IoT devices, such as TV streaming devices, digital projectors, aftermarket vehicle infotainment systems, digital picture frames and other products. Most of the infected devices were manufactured in China."
If you are buying any IoT products on Amazon, Temu, Shein, Alibaba, or almost anywhere, the product could have secret back doors that send information to criminals or allow criminals access to your home network.
There will be new ways in the future to know if an IoT product is secure. The U.S. and other countries have cyber labelling where companies can show they build secure IoT products, but the U.S. Cyber Trust Mark labelling program isn't fully in place yet. I'll let you know when products start to be announced.
In the meantime, the FBI suggests to look for these indicators. (The word, "indicators", is a common term we use in the cyber world.) The sentences in italics are my additional explanation.
The presence of suspicious marketplaces where apps are downloaded. This means the manufacturer doesn't use the official Google Play store to download software.
Requiring Google Play protect settings to be disabled. This is so the manufacturer can bypass security.
Generic TV streaming devices advertised as unlocked or capable of accessing free content. It's not truly free if you are helping criminals.
IoT devices advertised from unrecognizable brands. Purchase only brands you recognize that have been around for several decades.
Android devices that are not Play Protect certified. I'll write an article about Google Play Protect in the future.
Unexplained or suspicious Internet traffic. This one is hard to know unless you have technical network expertise.
Buying cheap IoT products is helping criminals get into our homes. If you have a question about a specific IoT device, please ask me and I'll do some research.
Toll fee scam: What you can learn from it
I think everyone who has a cell phone has probably gotten the Toll Pass scam, but I still wanted to talk about it just in case. It also gives me an opportunity to show how to identify scams.
Here is a screen capture of a very long text I received where I supposedly did not pay my tolls.
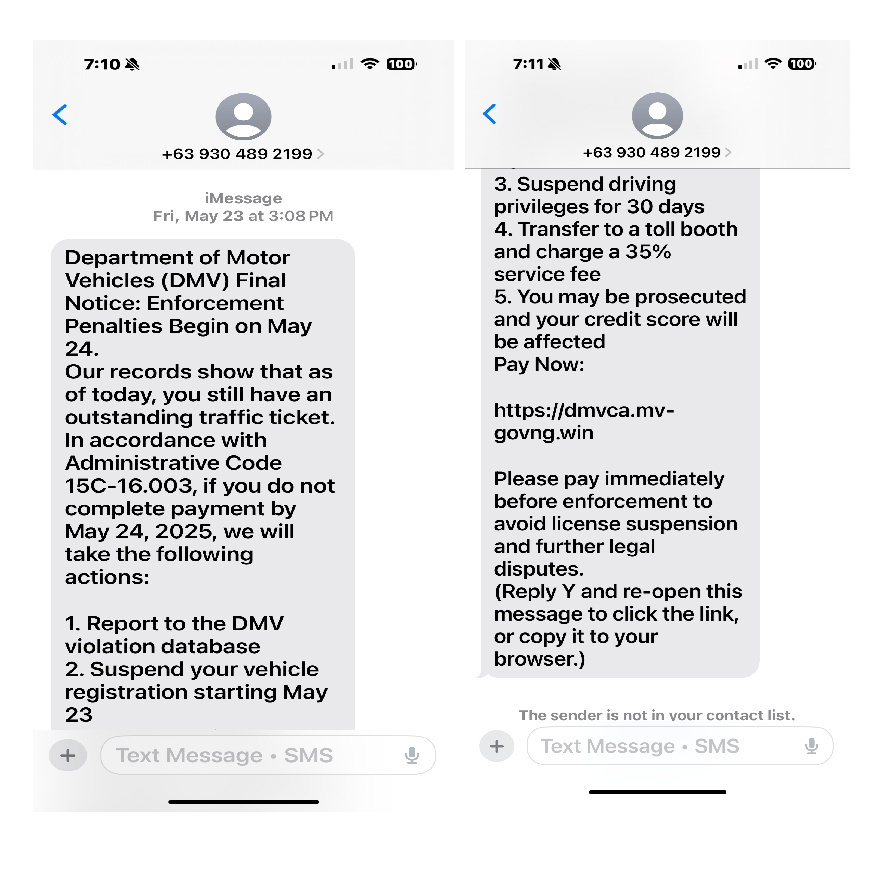
The first obvious scam indicator is the +63 country code. Why would I be getting a notice about tolls from a Philippines area code? If the toll systems even had my phone number (which they don't!), I'm sure the text would come from a US area code.
Now look at the URL they give: dmvca.mv-govng.win
On first look you see dmvca which could mean the Department of Motor vehicles in California. It's trying to fool you though and I'll show you how.
A web address is often just two parts: yahoo.com
Yahoo is the "domain" name and .com is the "domain extension". If I type www.yahoo.com, the www means I want to go to the web portion of Yahoo. To get to Yahoo's email, I can type mail.yahoo.com. That mail beginning part (called a "sub-domain") is a specific location in Yahoo.com.
Back to the toll pass scam example. The .win is a domain extension usually used by betting websites.
The website domain name is mv-govng. The full website is mv-govng.win.
And then the subdomain they created, dmvca, is meant to trick you into thinking it's the real California DMV. Thus dmvca.mv-govng.win is a real website location, but specifically built to scam you.
Scams are usually around for just a few hours or days before they are moved. When I pasted mv-govng.win into the Bitdefender link checker, it shows the website is safe.
I then tried to go to the website directly and it wouldn't show anything (it said there was no data). The scammers had removed the website data, but they still own the website.
For curiosity, I went to the official international registration organization for URLs, called ICANN, and did a "lookup" to see more about the domain.
The mv-govng.win domain was bought/created on May 23rd, the same day I received the text.
The other information in the domain registration is gibberish and the additional suspicious information is that the registrar is out of Hong Kong (not the US or even the Philippines).
So remember, every text you get from someone you don't know could be a scam or threat. Look at the following every time:
Phone number - even real phone numbers can be "spoofed" so that it may appear to come from the real company.
Links - always be suspicious!
Sense of urgency - see how they said I had to do something by the next day or my license would be suspended.
Be your own detective the next time you get a text. It can be fun!
Do you have an idea for a future newsletter? Please reply to this email and let me know.
Thank you so much!
Sincerely,
Cassie Crossley
Founder, Cyber Safe Center
https://www.cybersafecenter.com

